This blog is part of a Channel Partners Conference & Expo/MSP Summit sponsorship.
This week Gartner weighed in on a technology that unfortunately became a dreaded three-letter word over the past couple of years, XDR, by issuing its official Market Guide. In the guide, Gartner describes what an XDR consists of and discusses how organizations should view this technology in context with everything else they currently use or might use in the future. You can download your complimentary copy of the guide here to get into all the details, but in the meantime, here are a few key takeaways from my perspective.
XDR Must-Haves
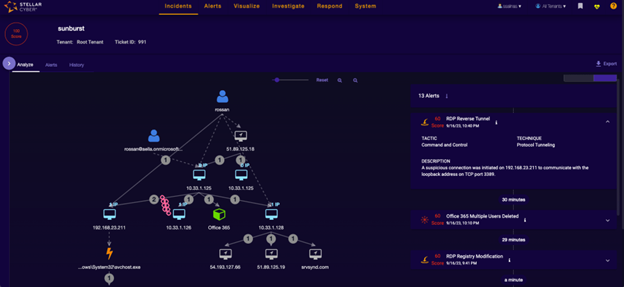
If you have followed the XDR soap opera, you know there are warring factions regarding the foundation of XDR. The Endpointers see XDR as an evolution of EDR with a firm belief that an XDR must have an embedded EDR as its foundation. The Networkers take a “network-first’ stance claiming XDR must begin with network visibility. Yet another faction, let’s call them the Wildcards, claim that whatever technology they develop is the foundation of XDR, from threat intelligence to email security and everything in between. As these factions produce marketing collateral and flashy animated videos, the potential buyers of XDR only get further confused. In the guide, Gartner doesn’t take a firm stance on which faction is right or wrong but instead identifies XDR must-haves.
Here are a few of the most important ones:
- XDRs must integrate threat intelligence and telemetry data from multiple sources with security analytics to contextualize and correlate security alerts.
- XDRs must include native sensors
- XDRs must deliver value above and beyond what you are currently using
The nice thing about having a concise “must-have” list is the ease with which vendors that do not, at a minimum, check the boxes for each requirement can be eliminated from serious consideration.